In the opening statements, Judith Klavans explained the design and goals of the workshop, noting that its primary concern was access management rather than rights management, as originally announced. Donald Waters explained that systems for access management include two key technical components, authentication and authorization. He noted that the focus of this workshop was on mechanisms for authorization. He outlined issues and options identified through a parallel initiative at CNI, the development of a White Paper on Authentication and Access Management Issues in Cross-organizational Use of Networked Information Resources. Waters reminded participants that the two scenarios presented in the workshop handout should stimulate discussions later in the day.
Two invited presentations set the stage for the discussions. Russell Vaught, director of Academic Computing at Penn State University, described the enterprise-wide authorization database in use at Penn State. John Erickson, Vice President for Systems Development at Yankee Book Peddler, Inc., described the goal of the Rights Metadata Working Group established as part of the joint activities of the National Information Standards Organization (NISO) and the International DOI (Digital Object Identifier) Foundation. In particular, he presented the conceptual model developed by the group to represent rights transactions and a proposed schema for rights operations.
Three groups were formed for two breakout sessions. Each group reflected a balance of expertise and was instructed to use the same approach, outlined in the handout, to examine the two scenarios. In the first breakout session, they were to consider both scenarios from the perspective of users. For the second, their task was to concentrate on the provider’s perspective. In the event, it proved hard to draw such lines. Perhaps because the challenge is to find a balance between the perspectives, the natural instinct was to consider both sides of issues such as security and privacy. At the same time, it was immediately apparent that the perspective of the library or institutional user differs markedly from that of the individual end user. In view of this complexity, the report summarizes the discussions from a thematic rather than a chronological standpoint.
Each breakout was followed by a plenary session at which a representative from each group summarized the discussions. Before the final discussion, Peter Jaszi of the Washington College of Law, American University, presented an update on legislative activities concerning copyright and related intellectual property rights (see appendix C).
Opening Statements
Judith Klavans, Director, Center for Research on Information Access, Columbia University
As a backdrop for discussion, Judith Klavans highlighted the findings of two previous workshops on topics related to access management. The first, a two-day workshop on Technology of Terms and Conditions, was held in September 1996. This workshop, which Klavans chaired with Jim Davis of Xerox PARC, was also funded by NSF. Roughly 30 participants explored issues from multidisciplinary perspectives. Four breakout groups focused on different aspects of the overall problem, covering the following topics: infrastructure requirements and the factors that encourage or inhibit acceptance of systems for managing terms and conditions; the technical, political, and social uncertainties that prevent the formulation of descriptions of terms and conditions; issues of scale; and ways to express conditions of use.
Of the conclusions reached, three in particular gave stimulus to the present workshop:
- publishers vary in their approaches to licensing and the degree of control they wish to retain,
- user communities must be involved in design and testing, and
- community attitudes and acceptance are of prime importance.
Other important points raised in September 1996 were that technology must accommodate vagueness and ambiguity; ambiguity may be intentional, as a consequence of the legal needs for flexible interpretation; economic pressures push publishers and libraries in opposite directions, and legal and technological developments will affect the economic balance; and international perspectives must be considered.
In December 1996, the Digital Library Federation (then the National Digital Library Federation) and researchers from the six projects funded through the first phase of the Digital Libraries Initiative held a joint meeting at Stanford University. A discussion of terms and conditions focused on points of disagreement and other issues preventing progress in building systems to manage access to information in digital libraries. Participants explored requirements from three perspectives: publishing, libraries, and technology. Publishing needs included a link to systems for digital commerce, a legal infrastructure that offered protection for digital contents, and technical mechanisms for controlling and describing digital content objects. Libraries needed mechanisms for authenticating users and roles, the association of new metadata elements with digital content objects to support self-management, and systems that allow for third-party rights. From a technological perspective, it was argued that progress would be made by ignoring some complexities, partitioning the problem, and discarding (or deferring) intractable parts.
The present DLF-NSF workshop, Klavans continued, would undoubtedly contribute to the development of the CNI White Paper. In the longer term, the findings would influence ongoing collaborative projects in which participants are engaged and would guide the planning and evaluation of access management components of other digital library projects.
Donald Waters, Director, Digital Library Federation
Donald Waters opened with a brief description of the Digital Library Federation, a consortium composed of the Library of Congress, the National Archives, the New York Public Library, and sixteen of the nation’s large research libraries. This organization was formed in 1995 to take the lead in identifying and lowering the barriers to federating digital libraries. One such barrier, said Waters, is the lack of adequate systems for access management, particularly for authorization. He emphasized that access management entails both authentication and authorization and presented a diagram to illustrate the elements of access management (see figure 2). Authentication refers to two distinct processes: verifying the identity of a user and ensuring that content is what it purports to be. Authorization ensures that terms and conditions in an agreement are being met by relating roles associated with a user to properties of an object.
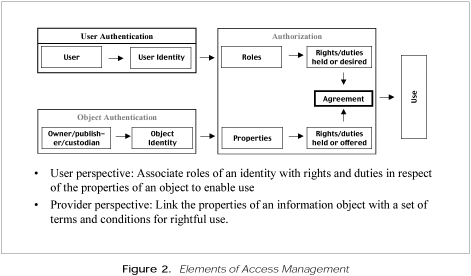
Waters asked participants to focus on authorization within the context of access management. Participants could evaluate specific scenarios, he suggested, by drawing on the draft CNI White Paper edited by Clifford Lynch, which recommends that the following factors be considered in evaluating approaches to access management in universities: granularity or degree of role distinction required, privacy, strength of security, manageability with respect to accountability and ability to collect management data, technical feasibility, and affordability.
The White Paper identifies three approaches used on campuses to support authentication and facilitate authorization by remote information services or resources.
- IP source filtering: the institution warrants that traffic from a given set of Internet addresses is legitimate.
- Proxies: the institution provides a specific machine through which all traffic to and from a service is routed and ensures that only legitimate traffic is permitted.
- Credentials: each user presents a credential (such as a user ID and password or a digital certificate) to warrant legitimacy.
Waters then introduced the two scenarios and specific questions to be addressed in the breakout sessions (see handout reproduced as figure 1). The terms authentication, authorization, and others associated with access management are defined in appendix D, compiled from definitions used by Waters and the other presenters at this workshop, by the DOI Rights Metadata Working Group, and by Clifford Lynch in the draft CNI White Paper.

