The following definitions have been compiled from those used by Waters and the other presenters at this workshop, by the DOI Rights Metadata Working Group, and by Clifford Lynch in the draft CNI White Paper.
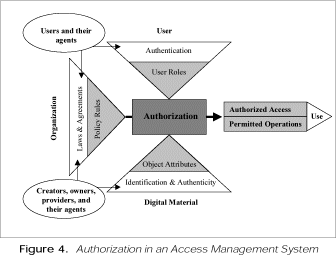
Terms with an asterisk are used in figure 4, which was drawn up following the workshop as a result of discussions among Donald Waters, John Erickson, William Arms, and Caroline Arms. Figure 4 combines elements of diagrams presented by Waters and Erickson at this workshop (figures 2 and 3) and in William Arms’s February 1998 article in D-Lib Magazine, “Implementing Policies for Access Management.” The grey boxes represent components of an automated authorization system, whereas the white boxes represent the interactions between users and providers in the external environment or between either party and the access management system.
Access Management
Access management is a process mediated by information managers by which users gain authorized access to the intellectual property of creators/owners/providers. Access management systems make use of authentication and authorization services to enable or control access to and use of a networked resource.
*Agreements
In figure 4, the term agreements refers to licenses and other legal agreements, entered into by or on behalf of users with information providers. Agreements may be made in different ways, for example, through formal contract or acceptance of terms at time of access. Within an automated access management system, the agreement and applicable laws will be implemented through a set of policy rules.
The DOI Rights Metadata Working Group uses the term both for a legal agreement between the parties and the corresponding representation of rules that control access within a system. For that group, “an Agreement is a statement of permitted operations, and applicable terms, for a given object or set of objects, and a given user or set of users. The default Agreement is that for ‘all users’, probably permitting a limited set of operations at standard fees. A site license that is already in place would be a specific Agreement.”
*Authentication of users
Authentication is the process whereby a network user establishes a right to an identity or name (such as a user ID, or credit card number). A user can establish this right through
something he or she knows (user ID and password),
something he or she has (ID card), or
something he or she is (handprint or retina scan).
*Authenticity of content
The authenticity of digital content requires mechanisms to assure users that content has not been corrupted. Since digital content is easily manipulated in ways that cannot be easily detected, users will expect publishers and third party custodians of information to provide assurances of authenticity.
*Authorization
Authorization is the process of determining whether an identity (given a set of role attributes associated with that identity) is permitted to perform some action, such as accessing a resource. The identity may represent a particular individual or be anonymous or pseudonymous. In the context of access management, authorization will rely on access policy rules, role attributes of the user, and terms and conditions attributes of a digital object to determine whether the desired action is permitted and how to disseminate the material.
Credential
In the context of access management, a credential is something that a user can present to an authorization system operated by an information provider as evidence of legitimacy. One form of credential is a user ID together with password. Another is a digital certificate following the X.509 standard. Support for transmitting such certificates and using them to control access is being incorporated into the latest versions of Web browsers and Web servers. See the CNI White Paper for more discussion.
*Object attributes
If access to certain digital material is to be managed, metadata attributes must be associated with each digital content object to indicate what terms and conditions apply to that object. An attribute would typically indicate a class of material to which an object belongs, with a common set of terms and conditions applying to all material in that class.
Operation
In the context of access management, an operation is any act that can be done with an object, internal or external, to a given computer system. Examples: view, print, save; modify, redistribute. (This definition is from the DOI Rights Metadata Working Group.) The word action is sometimes used in roughly the same way.
*Policy rules
Within in an access management system, policy rules are encoded to determine whether a user is entitled to access the digital object being requested and whether the requested operation is permitted. Policy rules operationalize agreements, such as licenses, and applicable law.
Proxy
In the context of access management, a proxy is a special computer that acts as a gateway to one or more resources. The licensee organization (or its agent) typically deploys a proxy. The proxy relies on authentication services to establish the legitimacy of a user and then routes all traffic between that user and the licensed resource. See the CNI White Paper for more discussion.
*Role
In the context of access management, role is specified by attributes associated with a user’s identity. Examples of role attributes are: membership in a university community, fulltime student, or individual subscriber to a scholarly journal. Authorization mechanisms use role attributes to determine whether a user is permitted to perform certain actions or operations on a resource or content object.
*Use
Use of a digital resource may extend beyond the operations performed online by a user when accessing a digital object. A faculty member who has printed a copy of an article may, for example, use it for personal reference or to make fifty copies for distribution to a class. Access management systems can limit access and have the potential to limit online operations; systems cannot fully control subsequent use.

